© 2023 Eclypsium, Inc.
Organizations need a better way to manage supply chain risk when it comes to their IT infrastructure.
Vendor questionnaires are poor inputs. And even when SBOMs are available, they don’t tell the whole story.
There isn’t an easy way to assess the risk for products such as laptops, servers, network equipment, or cloud software.
Assess the Risk of IT Products Easily
Eclypsium provides the industry’s first supply chain intelligence solution. Now, you can easily make more cost-effective and risk-based purchase decisions, as well as assess your exposure to new supply chain incidents and vulnerabilities.
Bring Hard Data to IT Purchase Decisions
Use supply chain intelligence to make risk-informed decisions when deciding between IT vendors.
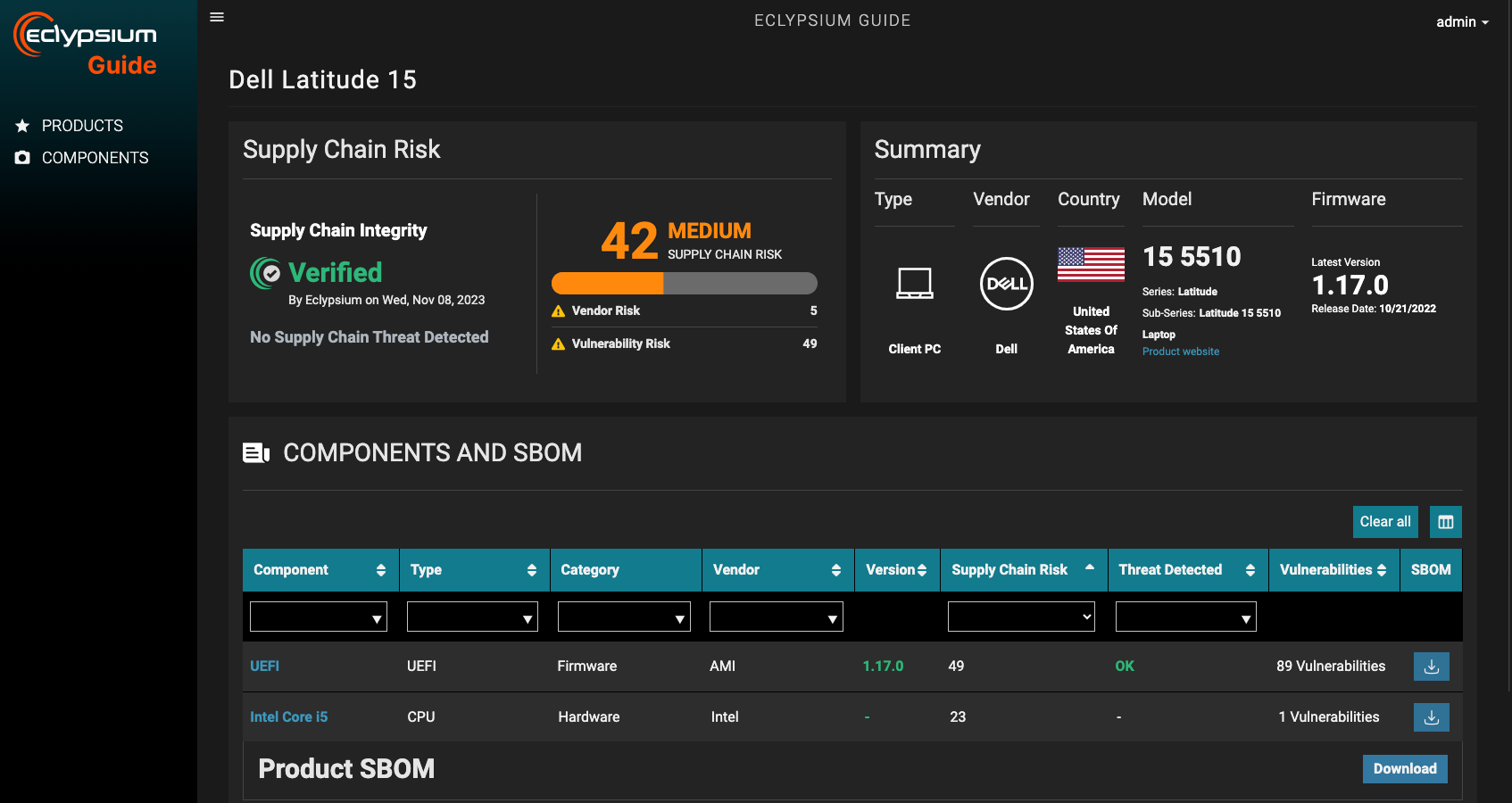
Today, vendor risk assessments rely primarily on external audits and questionnaires. The Eclypsium supply chain intelligence guide provides you with hard, technical data to measure the risk of IT infrastructure products. See the vulnerabilities present in the hardware, firmware, and software components.
Go Beyond SBOMs
- Assess new product risk based on component risk, vulnerabilities, security advisories, supply chain incidents, geographic provenance, etc.
- Verify product bills of material including hardware (HBOM), firmware (FBOM), and software (SBOM) components
- See version update history for products and components
Evaluate Exposure to New Supply Chain Incidents
The Eclypsium Guide provides you with up-to-date vulnerability data for hardware, firmware, and software components.
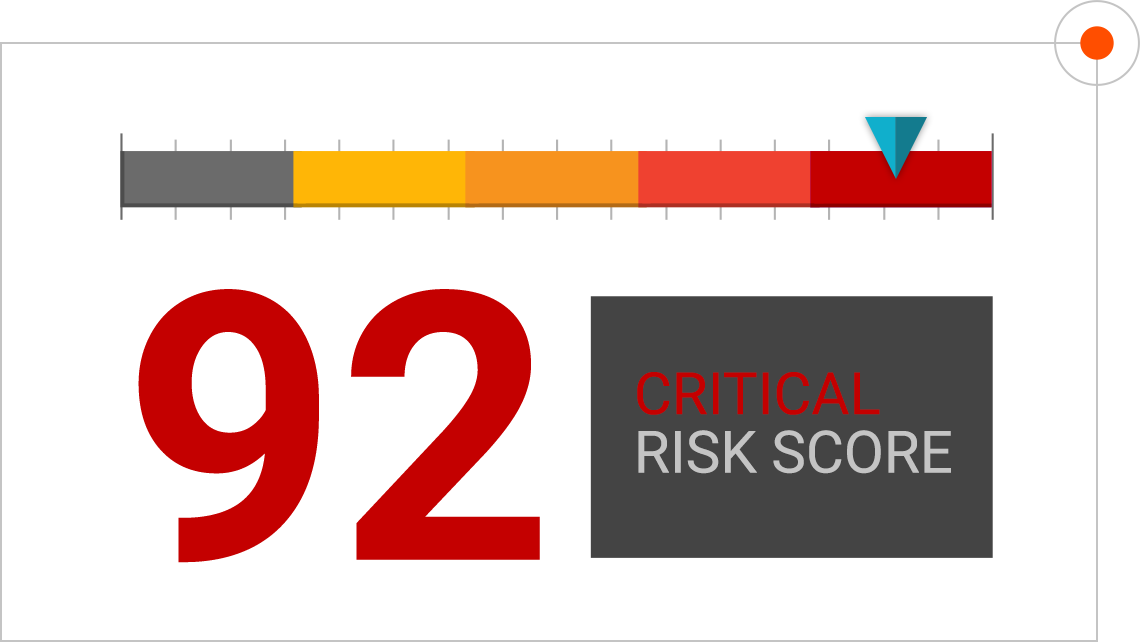
When a new supply chain threat or vulnerability is discovered in one of the third-party products or components, you have all the information you need to evaluate which IT products are affected and to deal with this threat or vulnerability. For example, if a specific component is found to have been altered by a threat actor, you can find out which products use that exact component.
Quickly Assess Supply Chain Risk Exposure
- Get all information about the new supply chain vulnerability or a threat and correlate with components and products
- Quickly find which products use vulnerable or compromised component and assess your exposure
- Use only firmware and software binaries and updated with verified integrity and assessed for threat or backdoor
Spend Your IT Budget Wisely
When it comes time to consider a refresh of your laptop or server fleet, you need insights into specifications and the potential lifespan of products.
The Eclypsium Guide makes it easy to answer questions in one place. Use the guide to select vendors that offer longer supported lifespans of devices, thereby lowering TCO.
Understand a Product’s True Cost
- Estimate support window based on update history
- View the components used in a product
- Factor potential supply chain risk into the equation
Get Early Access to the Guide
Take the first step in your journey to address digital supply chain risks and build a supply chain security program for your organization.